CSR Performances
Content
Along with the rapidly changing technology and intensifying competition in the market, fair business with stakeholders such as suppliers, and competitors has become more important. Fair business is not a simple ethical issue but a sustainability issue of growing importance.
Our Approach
ISU PETASYS has established the Code of Conduct as a standard for fair business operations and also various systems to comply with the standard. Moreover, the company has strengthened the management of CSR in the supply chain to minimize the risk of fair business operations and build a virtuous circle of social responsibility.
Management System
ISU PETASYS has established a fair and transparent business operating system in an effort to fulfill its social responsibility. The company complies with laws and regulations on business operations as well as international ethical standards by establishing a code of ethics, CSR regulations, and whistleblowing system. In addition, the company has enacted the Code of Conduct to promote the fair corporate culture among employees.
Compliance
ISU PETASYS complies with the laws and regulations of the countries of its business operations, and reduces risk factors in business operations through the internal audit system. Furthermore, the company has operated the internal control system to follow the international ethical practices and standards.
Internal control system
ISU PETASYS has regularly checked the key control items of each task related to fair business operations and separately operated the internal control system for a smooth control process. Moreover, the company has maintained the reliability and transparency of accounting information through the internal accounting management system.
Anti-corruption
ISU PETASYS prohibits employees from engaging in bribe, corruption, coercion and embezzlement, and from providing or receiving bribes or other advantages to enjoy improper and illegal benefits. As a result of these efforts, not a single case of corruption occurred during the report period.
Anti-corruption&bribery policy
ANTI-CORRUPTION & BRIBERY POLICY
1. PURPOSE
ISU Petasys is prohibited from operating or accepting every type of corruption both in direct or indirect manner covering every business and related department in every country.
All employees must comply with Anti-corruption & bribery policy, remove the risk of corruption, and conduct anti-corruption management system.
2. APPLICABLE LAWS
Employees of ISU Petasys must abide by all applicable anti-bribery laws, including 「Korean Criminal Code」, 「Additional Punishment Law on Specific Crimes」, 「Convention on Combating Bribery of Foreign Public Officials in International Business Transactions」, 「Improper Solicitation and Graft Act」, 「America Foreign Corrupt Practices Act」, 「British Bribery Act」 and the local laws in every country in which we do business.
3. RESPONSIBILITY OF MANAGER
ISU Petasys assigns a manager of anti-corruption & bribery who has an independent authority and responsibility. The manager must advise and manage to solve the problems of anti-corruption & bribery management system.
4. IMPLEMENTATION
ISU Petasys must prevent the violation of the anti-corruption & bribery policy to operate anti corruption management system, and continuously improve. All directors, officers, employees and contractors of ISU Petasys will provide certification of compliance with this Policy.
5. CONSEQUENCES OF NON-COMPLIANCE WITH THE POLICY
In case the employees of ISU Petasys break the laws or policy of anti-corruption & bribery, or even if there is no reasonable action of employees after finding violation of the laws and policy; ISU Petasys will not be responsible for the violation, and will take disciplinary action against them to uphold the internal regulation.
6. PROTECTING IDENTITY OF WHISTLEBLOWER
ISU Petasys keeps the whistleblowers’ personal information confidentially, and project the whistleblowers from unfair treatment due to reporting corruption and bribery. Contribution of saving anti-corruption & bribery policy will be considered in the evaluation process.

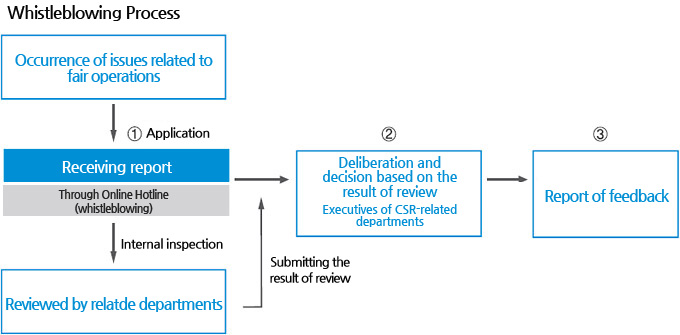
Whistleblowing System
ISU PETASYS has introduced a whistle blowing system to ensure that internal and external stakeholders can freely report any kind of unfair business activities including corruption. Stakeholders of ISU PETASYS including employees, customers, and suppliers can submit an anonymous report to protect whistleblowers according to the internal CSR regulations. In 2016, one case was submitted and handled according to the process.
Mutual Growth
ISU PETASYS promotes mutual growth with its suppliers considering them as a group bound by a common destiny. The company operates training programs and communication channels for its suppliers based on the values of common destiny, fair management, pursuit of goal, and mutual innovation.
CSR Management in the Supply Chain
CSR Management Standards in the Supply Chain
ISU PETASYS has established the CSR management standards and applied them to the supplier management procedures. The company will strengthen its CSR management from a mutual growth perspective so that its suppliers can build a safe working environment and pursue environmentally- friendly and ethical business operations.
CSR Audit for Suppliers
ISU PETASYS conducts CSR audits to fulfill its social responsibility throughout the supply chain. By carrying out audits in four areas of human rights and labor, environment · safety · health, fair business operations, and product responsibility, the company strives to reduce risks that might occur in the supply chain and consolidate the foundation for sustainable management.
Customer Information and Technology Protection
ISU PETASYS has actively engaged in the protection of information assets by incorporating information security into its corporate management. By tightening the control of administrative security, physical security, and technical security, the company is committed to protecting customer information and technology from various threats, such as information leakage, exposure, modulation, delay, and disaster.

